
KyberSwap has identified and neutralized an exploit discovered on our frontend. Please find the timeline of events, identified attackers and affected users, and necessary actions below.
There is no vulnerability in our smart contracts.
Timeline of Events
On 1 Sep, 3.24PM GMT+7, we identified a suspicious element on our frontend. Shutting down our front end to conduct investigations, we identified a malicious code in our Google Tag Manager (GTM) which inserted a false approval, allowing a hacker to transfer a user’s funds to his address.
At 4pm GMT+7 we announced to our community that we had disabled the UI, during which we investigated the cause of the frontend exploit. A malicious code in our GTM was identified upon which we disabled GTM.
Conducting further checks, we found that after disabling GTM, the bad script was eliminated with no further suspicious activity. The script had been discreetly injected and specifically targeting whale wallets with large amounts. We restored the UI, with the steps after to identify all of the attackers’ addresses, and identify the extent of the damage, and which addresses were affected. We announced the UI going live again at 5.46pm GMT+7. We are continuing to conduct further investigations and working with security experts to ensure the highest standards of security.
Confirmed Attacker Addresses & Suspected Attacker Addresses Identified:
- Attacker’s address:
– 0x57A72cE4fd69eBEdEfC1a938b690fbf11A7Dff80 (Polygon & Ethereum)(Confirmed) - Address receiving tokens when 0x57A72cE4fd69eBEdEfC1a938b690fbf11A7Dff80 call transfer from:
– 0xfd6f294f3c9e117dde30495770ba9b073c33b065 (Polygon) (Confirmed)
– 0xb9943d5ab8b3a70925714233d938dd62e957f92e (Ethereum) (Confirmed) - Addresses supplying native tokens to 0x57A72cE4fd69eBEdEfC1a938b690fbf11A7Dff80 and other attacker’s (confirmed and suspected) address excluding all CEX addresses:
Polygon:
- 0x9bc22f7e0234029eaf2c570588d829f07123fdd6 (confirmed)
— Hack test address - 0x6fd64b2555fa6d1bf8564f728da7eae8ad1397b1 (suspected)
— Sent matic to 0x57A72cE4fd69eBEdEfC1a938b690fbf11A7Dff80
— https://opensea.io/Obolonchik
https://opensea.io/assets/matic/0xa9a6a3626993d487d2dbda3173cf58ca1a9d9e9f/87585141242935445043385798402757836623055821569575190448604925000384430867121 - 0x8152e9e1b7408b5f7c02ca54f85f245e7d013b5d (suspected)
— Sent matic to 0x57A72cE4fd69eBEdEfC1a938b690fbf11A7Dff80
— https://opensea.io/qwekurasa - 0x2f5173967e1fb95f936dfcd6400bc2e533cf3708 (suspected)
— Sent matic to 0x57A72cE4fd69eBEdEfC1a938b690fbf11A7Dff80
— https://opensea.io/maddmax77 - 0x97f0df5bd8c40cbb27c2631b269d507fadc49f34 (suspected)
— Sent matic to 0x57A72cE4fd69eBEdEfC1a938b690fbf11A7Dff80 - 0x60ef468b2704cfb75edc025531a03816cc69f99c (suspected)
— Sent matic to 0xfd6f294f3c9e117dde30495770ba9b073c33b065
https://opensea.io/0x60EF468B2704cFB75EdC025531a03816cC69f99C
Ethereum:
- 0x44183fd1a79704f79e0986c6380dd9bfbbc7e6d2 (confirmed)
— Hack test address
4. Attacker moved fund to BTC
– Transfer to BTC
https://live.blockcypher.com/btc/address/bc1q8gn5fuu2eva2cwmm5v5rqvqs39va44n3u7l6dp/
– Attacker sent the fund out, to a mixer/CEX
https://live.blockcypher.com/btc/tx/7e5708652dbea1bb985ede7f810adcf33eff138f47f63c6525a0801a4235b3c5/
Note: If you operate a central exchange or DeFi protocol, do block funds transfers from the attackers’ addresses above so as to help isolate the wallets. If you can ascertain the identity of the attacker based on the associated addresses, we appreciate you sharing this with us, to assist with the investigation.
Are funds safe?
We have identified US$265k worth of user funds that have been lost.
These numbers will be updated if any new information arises.
Who is affected?
The complete list of affected addresses is below:
- 0x6e2ff642d60d1c99811f0a1a39e1b0250c488cce (Polygon)
- 0x20fc9dd90ab50933537a68b9f059dbf543b107dc (Polygon)
This list will be updated if any new information arises.
Could more people be affected? Is it safe to use KyberSwap?
The attack was identified and put a stop to after 2 hours of investigations. This attack was an FE exploit and there is no smart contract vulnerability.
For now it is safe to use KyberSwap’s functions, with caution. When signing for approval, check the txn information. If the transaction is to give allowance, please ensure the allowance is given to the correct contract address.
List of Contracts Addresses Users may need to approve (token allowance, or NFT) in order to use KyberSwap services:
KyberSwap Elastic Position Manager — 0x2B1c7b41f6A8F2b2bc45C3233a5d5FB3cD6dC9A8
KyberSwap Classic Router — 0x5649B4DD00780e99Bab7Abb4A3d581Ea1aEB23D0
ZapIn for Classic — 0x83D4908c1B4F9Ca423BEE264163BC1d50F251c31
ZapIn for new Classic — 0x2abE8750e4a65584d7452316356128C936273e0D
KyberSwap MetaAggregator — 0x617Dee16B86534a5d792A4d7A62FB491B544111E
KyberSwap MetaAggregator — 0x180555D4d45e67520adC7c0c51b512c7A50877f2
KyberSwap MetaAggregator — 0x00555513Acf282B42882420E5e5bA87b44D8fA6E
KyberSwapElasticLM — 0x5C503D4b7DE0633f031229bbAA6A5e4A31cc35d8
KyberSwapElasticLM — 0xBdEc4a045446F583dc564C0A227FFd475b329bf0
FairLaunch for Classic farm — 0xa107e6466be74361840059a11e390200371a7538
If you sign a transaction and see the warning like the image, you should stop and tell the Kyber team immediately. Do not sign the transaction.
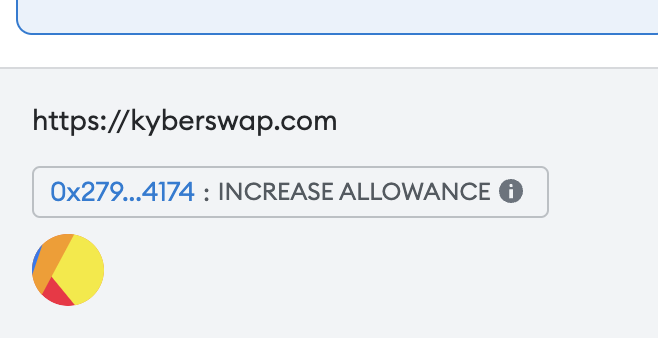
What should I do now?
If you are affected, follow the instructions to revoke the malicious approval, and contact the KyberSwap team in Discord for support. KyberSwap will compensate you for funds lost.
Instructions to Revoke Malicious Approval
On Ethereum
- Go to https://etherscan.io/tokenapprovalchecker input your wallet address for searching
- Check if you have any records that the Approved Spender is 0x57a72ce4fd69ebedefc1a938b690fbf11a7dff80.
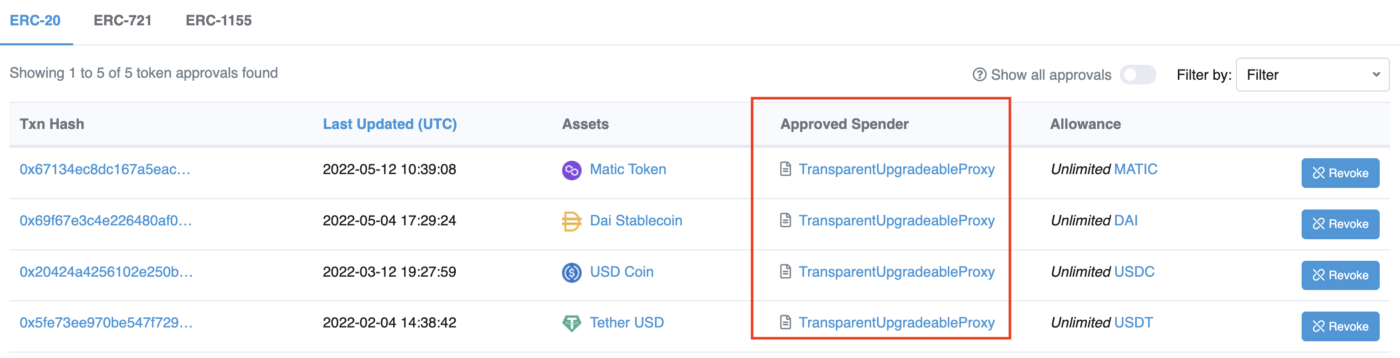
- If you don’t have any records, this address is safe and you can ignore next steps
- If you have any records as specified, go to the next step
- Connect your wallet by pressing the “Connect to Web3” button
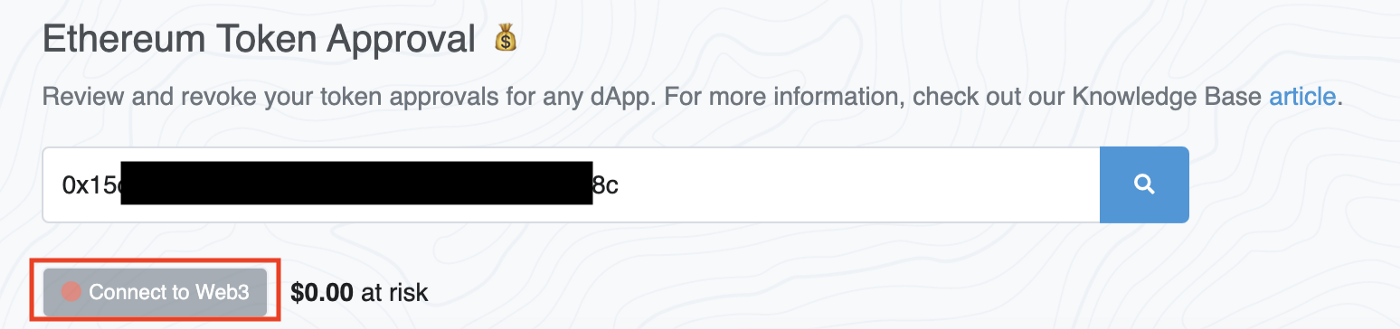
- Revoke all records that have the Approved Spender is 0x57a72ce4fd69ebedefc1a938b690fbf11a7dff80 by pressing the “Revoke” button on the right side and sign the revoked transactions in your wallet
- Details about steps with animation on how to revoke a spender here
- Make sure all your addresses are checked
On Polygon
- Go to https://polygonscan.com/tokenapprovalchecker, input your wallet address for searching
- Check if you have any records that the Approved Spender is 0x57a72ce4fd69ebedefc1a938b690fbf11a7dff80.
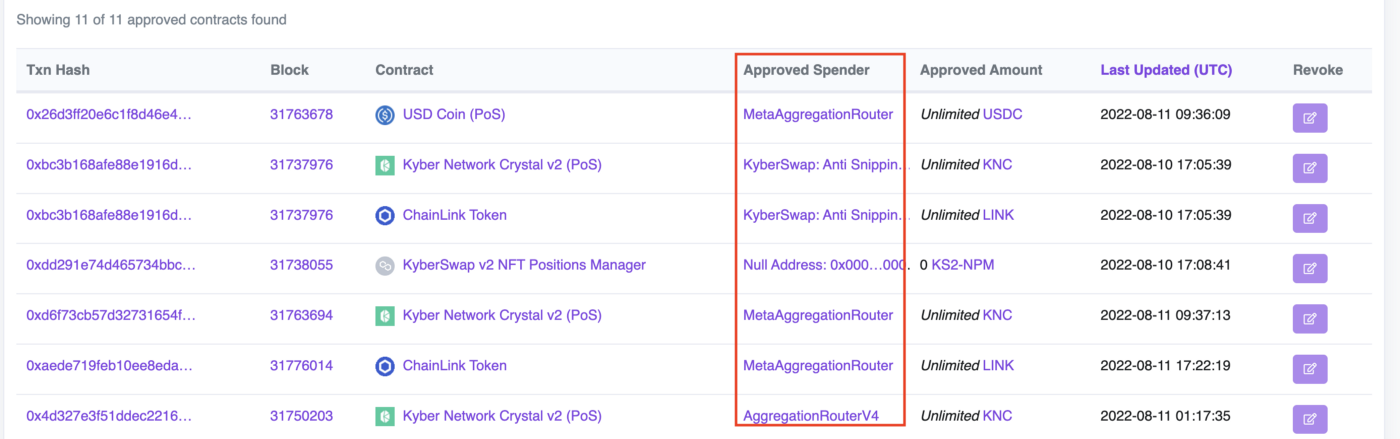
- If you don’t have any records, this address is safe and you can ignore next steps
- If you have any records as specified, go to the next step
- Connect your wallet by pressing the “Connect to Web3” button
- Revoke all records that have the Approved Spender is 0x57a72ce4fd69ebedefc1a938b690fbf11a7dff80 by pressing the “Revoke” button on the right side and sign the revoked transactions in your wallet
- Details about steps with animation on how to revoke a spender here
- Make sure all your addresses are checked
If I am affected, do I get compensated/my money back?
If your address and funds have been compromised KyberSwap will compensate you for funds lost. Please join our Discord channel to raise your case to our team.
What next?
Kyber Network is 100% committed to creating and maintaining a decentralized platform that is secure for users and partners, and today’s events show while our team has been swift to address the issue and is committed to making users whole, there is much to do to keep DeFi secure moving forward.
Forensic investigations are already under way to identify further information about the attackers, and KyberSwap is in touch with various exchanges to block any funds transfer from the attackers’ wallets and identify them. This attack does not affect our progress and operations moving forward.
User safety is of #1 priority to us, and if you or anyone you know are affected, please get in touch with us immediately via our Discord channel so we can note your case and provide support.
Message to Attacker
Hello attacker. We know the addresses you own have received funds from central exchanges and we can track you down from there. We also know the addresses you own have OpenSea profiles and we can track you through the NFT communities or directly through OpenSea. As the doors of exchanges close upon you, you will not be able to cash out without revealing yourself. As a bug bounty, we are offering you 15% of the funds if you return it and have a conversation with our team. To confirm, send the funds to the following Polygon address: 0x2dc0ba6ba3485edd61f17ffabf4c7a9626001d50



